Manage users using the GUI
Explore the management of users licensed to work with the WEKA system using the GUI.
Using the GUI, you can:
Manage local users
Local users are created in the local system instead of domain users that the organization's User Directory manages. You can create up to 1152 local users to work with a WEKA system cluster.
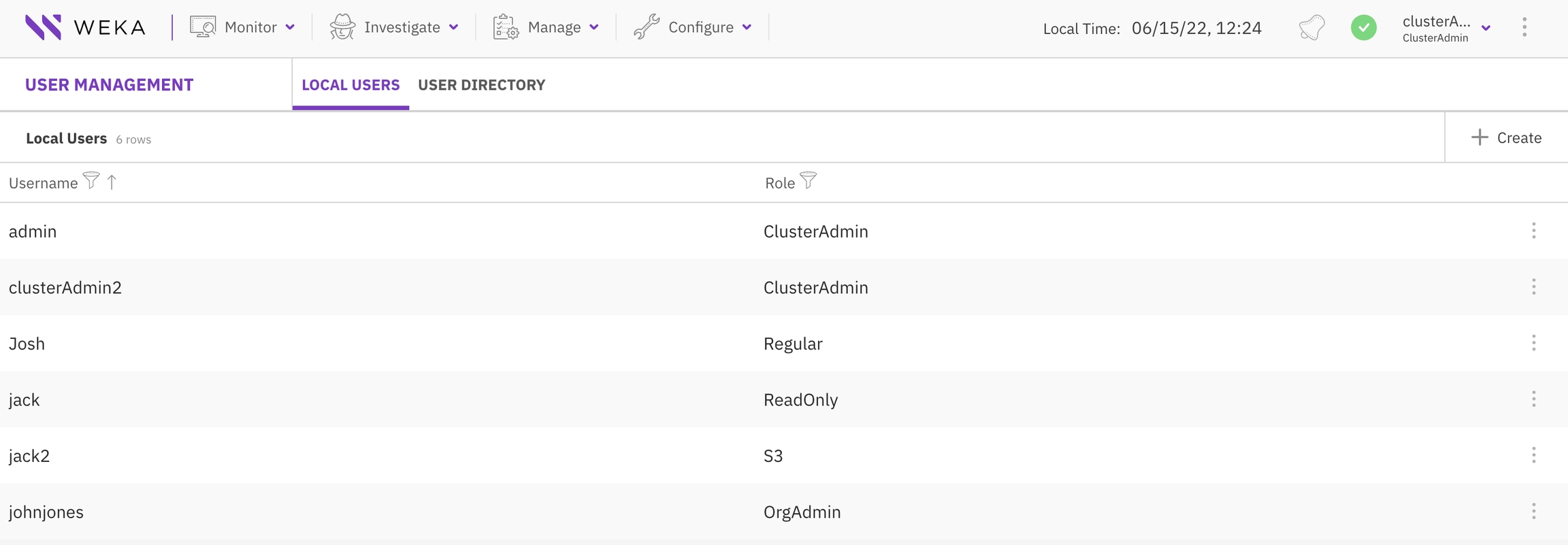
Create a local user
Procedure
From the menu, select Configure > User Management.
In the Local Users tab, select +Create.
In the Create New User dialog, set the following properties:
Username: Set the user name for the local user.
Password: Set a password according to the requirements. The password must contain at least 8 characters: an uppercase letter, a lowercase letter, and a number or a special character.
Confirm Password: Type the same password again.
Role: Select the role for the local user. If you select an S3 user role, select the relevant S3 policy and, optionally, the POSIX UID and POSIX GID.
Select Save.
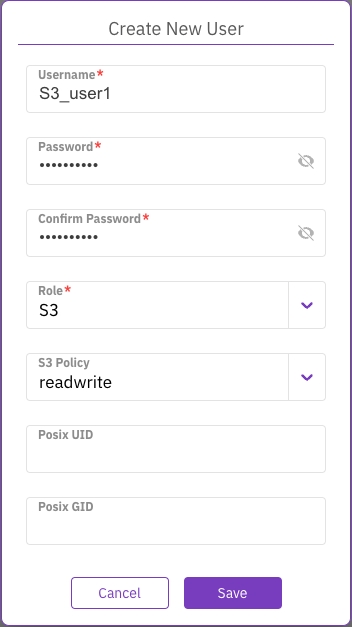
Edit a local user
You can modify the role of a local user but not your role (the signed-in user). For an S3 user, you can only modify the S3 policy, POSIX UID, and POSIX GID.
Procedure
In the Local Users tab, select the three dots of the local user you want to edit, then select Edit User.
From the Role property, select the required role. If you modify the role to S3, you can set the S3 policy, POSIX UID, and POSIX GID.
Select Save.
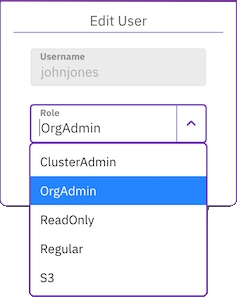
Change a local user password
As a Cluster Admin or Organization Admin, you can change the password of a local user and revoke the user's tokens.
To regain access to the system after changing the password, the user must re-authenticate using the new password.
Procedure
In the Local Users tab, select the three dots of the local user whose password you want to change, then select Change Password.
In the Change Password for a user dialog, set the following properties:
Old password: Set the old password.
Password: Set a new password according to the requirements.
Confirm Password: Type the same new password again.
Revoke Tokens: If the user's existing tokens are compromised, you can revoke all of the user's tokens and change their password. To regain access to the system, the user must re-authenticate with the new password or obtain new tokens through the API.
Select Save.
Change your password
You can change your password at any time.
Procedure
From the top bar, select the signed-in user, then select Change Password.

In the Change Password dialog, set the properties described in the Change a local user password topic.
Select Save.
Revoke local user tokens
If the user's existing tokens are compromised, you can revoke all the user's tokens, regardless of changing the user's password. To re-access the system, the user re-authenticates with the new password, or the user needs to obtain new tokens using the API.
Procedure
In the Local Users tab, select the three dots of the local user you want to revoke the user tokens, then select Revoke User Tokens.
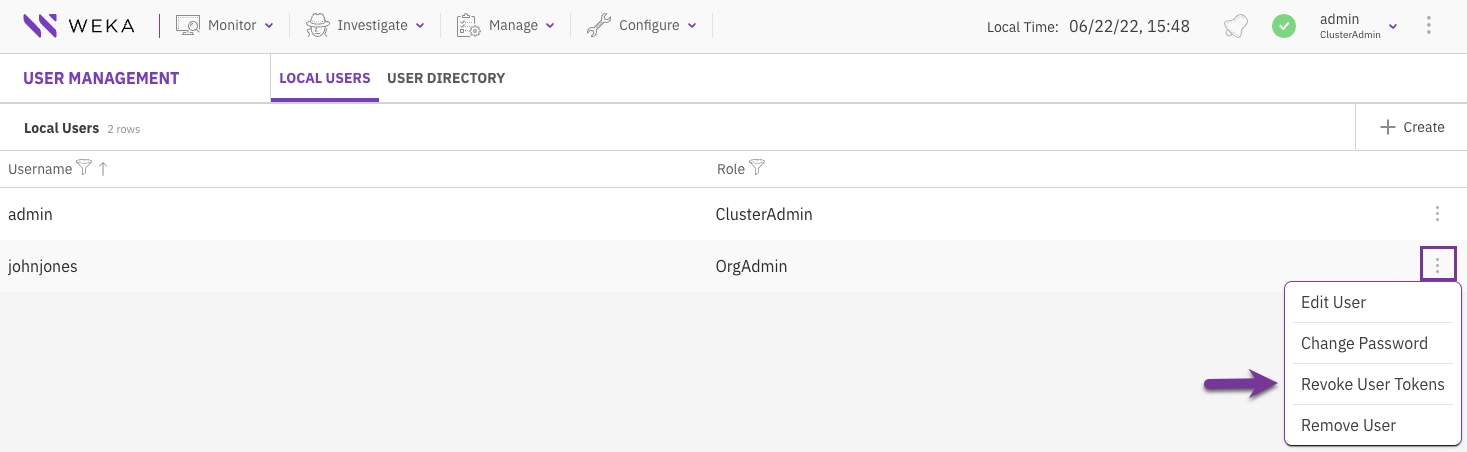
In the confirmation message, select Revoke Tokens.
Remove a local user
You can remove a local user that is no longer required.
Procedure
In the Local Users tab, select the three dots of the local user to remove, then select Remove User.
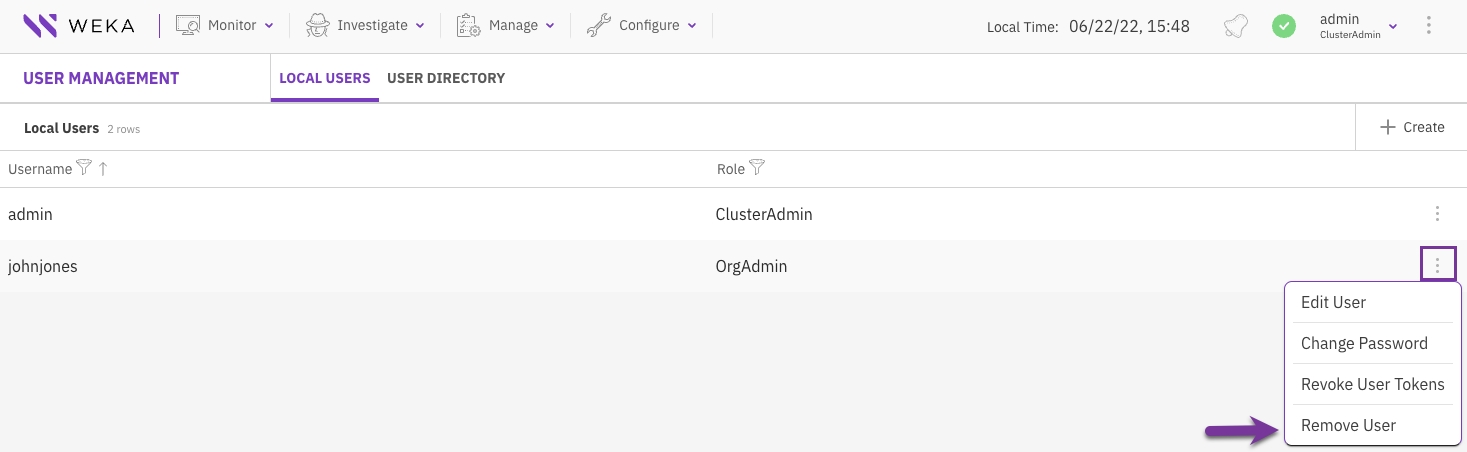
In the confirmation message, select Yes.
Manage user directory
You can set user access to the Weka system from the organization user directory, either by LDAP or Active Directory.
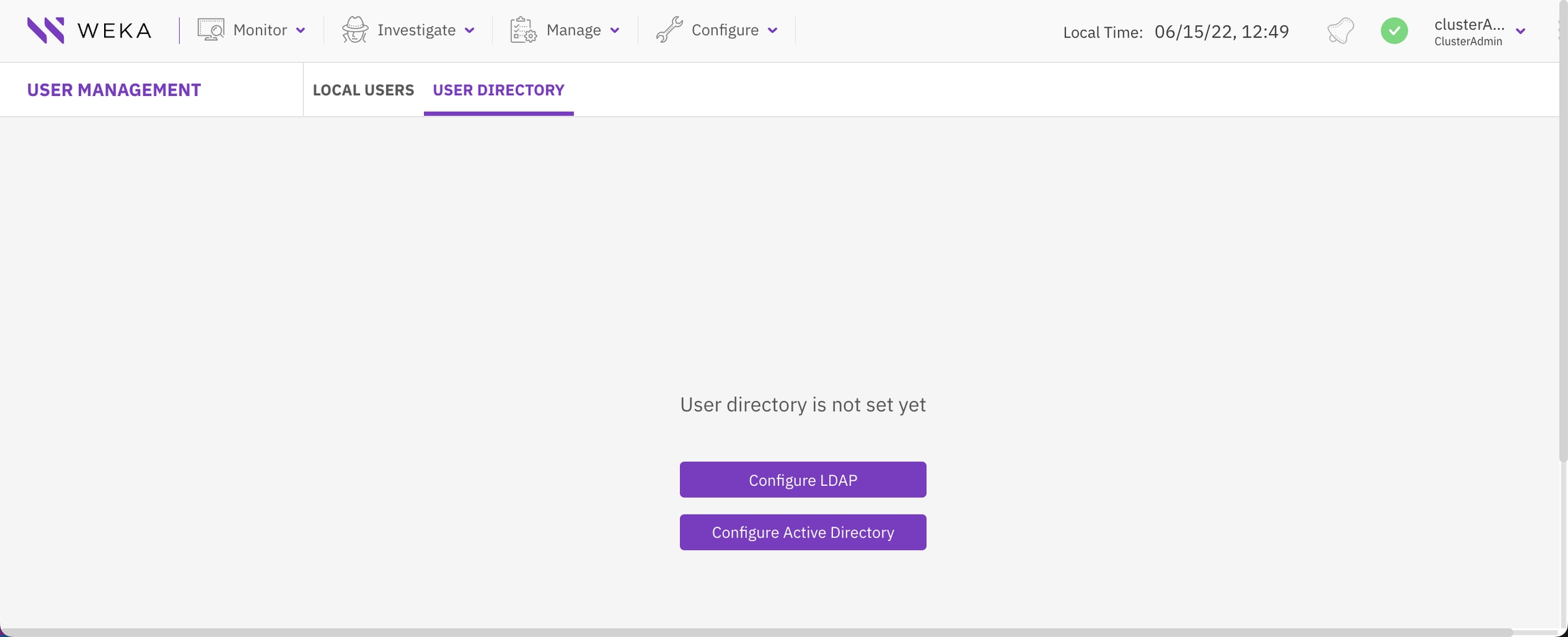
Configure LDAP
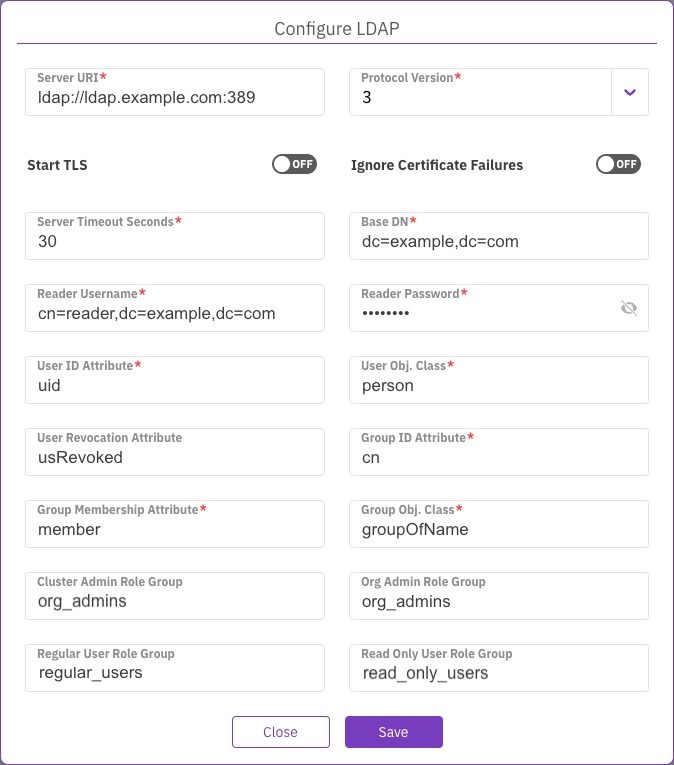
To use LDAP for authenticating users, set the property values based on your specific LDAP environment and configuration.
LDAP property descriptions
Server URI: The URI or address of the LDAP server, including the protocol (in this case, LDAP), the server's hostname or IP address, and the port number. Example value:
ldap://ldap.example.com:389Protocol Version: The version of the LDAP protocol being used. Common versions include LDAPv2 and LDAPv3. Example value:
3Start TLS: When enabled, this option initiates a Transport Layer Security (TLS) connection with the LDAP server. TLS provides encryption and secure communication between the client and server, protecting the confidentiality and integrity of data transmitted over the network.
Ignore Certificate Failures: When enabled, this option instructs the LDAP client to ignore certificate validation failures during the TLS/SSL handshake process. Certificate validation failures can include expired, self-signed, or mismatched certificates. Enabling this option allows the client to establish a connection even if the server's certificate cannot be fully validated. Use this option cautiously, as it may expose the connection to potential security risks.
Enabling Start TLS and Ignore Certificate Failures must be done based on your specific security requirements and the configuration of your LDAP server.
Server Timeout Seconds: The maximum amount of time, in seconds, the client waits for a response from the LDAP server before timing out. Example value:
30Base DN : The base distinguished name (DN) is the starting point for searching the directory tree. It represents the top-level entry in the LDAP directory. Example Value:
dc=example,dc=comReader Username: The username or distinguished name (DN) of a dedicated reader user account used for authenticating and reading data from the LDAP server. Example value:
cn=reader,dc=example,dc=comReader Password: The password is associated with the reader user account for authentication purposes. Example Value:
********User ID Attribute: The attribute in the LDAP schema that represents the unique identifier or username for user entries. Example value:
uidUser Object Class: The object class or object type in the LDAP schema defines the structure and attributes of user entries. Example value:
personUser Revocation Attribute: An attribute indicates a user account's revocation status, typically a boolean attribute set to true or false. Example value:
isRevokedGroup ID Attribute: The attribute in the LDAP schema represents the unique identifier or name for group entries. Example value:
cnGroup Membership Attribute: The attribute establishes the membership relationship between users and groups, specifying which users are members of a particular group. Example value:
memberGroup Object Class: The object class or object type in the LDAP schema defines the structure and attributes of group entries. Example value:
groupOfNamesCluster Admin Group: The LDAP group granted administrative privileges for managing the LDAP cluster. Example value:
cn=cluster_admins,ou=groups,dc=example,dc=com sAMAccountName: cluster_adminsOrganization Admin Role Group: The LDAP group granted administrative privileges for managing specific organizations or units within the LDAP directory. Example value:
cn=org_admins,ou=groups,dc=example,dc=com sAMAccountName: org_adminsRegular User Role Group: The group in LDAP represents regular users with standard access privileges. Example value:
cn=regular_users,ou=groups,dc=example,dc=com sAMAccountName: regular_usersRead-only User Role Group: The group in LDAP represents users with read-only access privileges restricted from making modifications. Example value:
cn=read_only_users,ou=groups,dc=example,dc=com sAMAccountName: read_only_users
Note: The sAMAccountName (user logon name) in the Cluster Admin, Organization Admin, Regular User, and Read-only User Role Groups can be up to 20 characters long.
Procedure
From the menu, select Configure > User Management.
Select the User Directory tab.
Select Configure LDAP.
Set all properties based on your specific LDAP environment and configuration.
Select Save.
Once the LDAP configuration is completed, the User Directory tab displays the details. You can disable the LDAP configuration, update the configuration, or reset the configuration values.
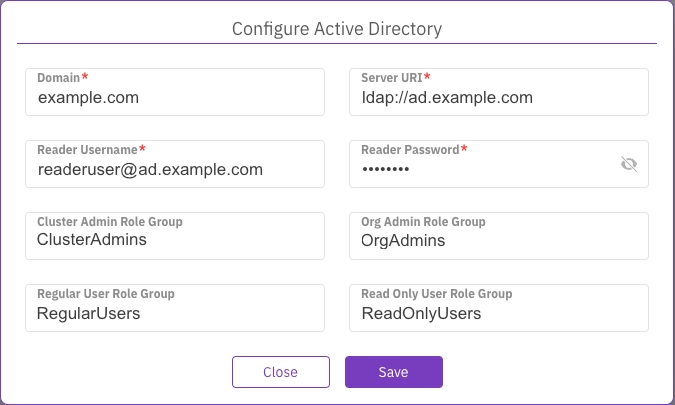
Configure Active Directory
To use Active Directory for authenticating users, set the property values based on your specific Active Directory environment and configuration.
Active Directory property descriptions
Domain: The domain name of the Active Directory environment. It represents the network boundary and provides a way to organize and manage resources, users, and groups. Example value:
example.comServer URI: The URI or address of the Active Directory server, including the protocol (in this case, LDAP) and the server's hostname or IP address. Example value:
ldap://ad.example.comReader Username: A dedicated reader user account's username or user principal name (UPN) used for authenticating and reading data from the Active Directory. Example value:
[email protected]Reader Password: The password associated with the reader user account for authentication purposes. Example Value:
********Cluster Admin Role Group: The group in Active Directory granted administrative privileges for managing the cluster or server infrastructure. Example value:
CN=ClusterAdmins,CN=Users,DC=example,DC=com sAMAccountName: ClusterAdminsOrganization Admin Role Group: The group in Active Directory granted administrative privileges for managing specific organizations or units within the Active Directory environment. Example value:
CN=OrgAdmins,CN=Users,DC=example,DC=com sAMAccountName: OrgAdminsRegular User Role Group: The group in Active Directory represents regular users with standard access privileges. Example value:
CN=RegularUsers,CN=Users,DC=example,DC=com sAMAccountName: RegularUsersRead-only User Role Group: The group in Active Directory represents users with read-only access privileges, restricted from making modifications. Example value:
CN=ReadOnlyUsers,CN=Users,DC=example,DC=com sAMAccountName: ReadOnlyUsers
Note: The sAMAccountName (user logon name) in the Cluster Admin, Organization Admin, Regular User, and Read-only User Role Groups can be up to 20 characters long.
Procedure
From the menu, select Configure > User Management.
Select the User Directory tab.
Select Configure Active Directory.
Set all properties based on your specific Active Directory environment and configuration.
Select Save.
Once the Active Directory configuration is completed, the User Directory tab displays the details. You can disable the Active Directory configuration, update the configuration, or reset the configuration values.
Last updated