Manage users using the GUI
Explore the GUI to manage local users and configure the user directories LDAP or AD.
Using the GUI, you can:
Manage local users
Local users are created in the local system instead of domain users that the organization's User Directory manages. You can create up to 1152 local users to work with a WEKA system cluster.

Create a local user
Procedure
From the menu, select Configure > User Management.
In the Local Users tab, select +Create.
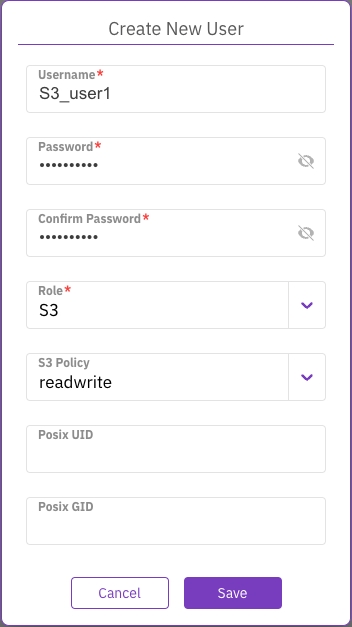
In the Create New User dialog, set the following properties:
Username: Set the user name for the local user.
Password: Set a password according to the requirements. The password must contain at least 8 characters: an uppercase letter, a lowercase letter, and a number or a special character.
Confirm Password: Type the same password again.
Role: Select the role for the local user. If you select an S3 user role, select the relevant S3 policy and, optionally, the and . For role details, see Role descriptions .
Select Save.
Edit a local user
You can modify the role of a local user but not your role (the signed-in user). For an S3 user, you can only modify the S3 policy, POSIX UID, and POSIX GID.
Procedure
In the Local Users tab, select the three dots of the local user you want to edit, then select Edit User.
From the Role property, select the required role. If you modify the role to S3, you can set the S3 policy, POSIX UID, and POSIX GID.
Select Save.

Change a local user password
As a Cluster Admin or Organization Admin, you can change the password of a local user and revoke the user's tokens.
Procedure
In the Local Users tab, select the three dots of the local user whose password you want to change, then select Change Password.
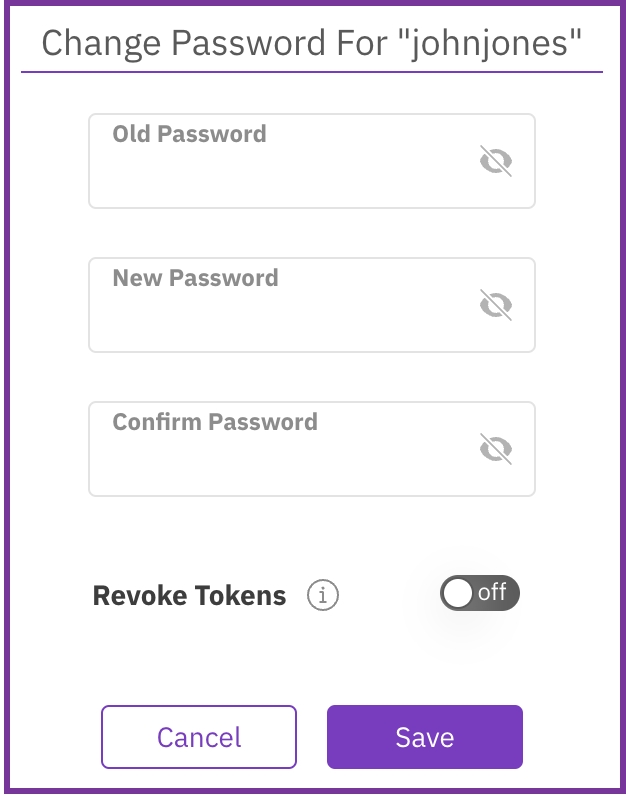
In the Change Password for a user dialog, set the following properties:
Old password: Set the old password.
Password: Set a new password according to the requirements.
Confirm Password: Type the same new password again.
Revoke Tokens: If the user's existing tokens are compromised, you can revoke all of the user's tokens and change their password. To regain access to the system, the user must re-authenticate with the new password or obtain new tokens through the API.
Select Save.
Change your password
You can change your password at any time.
Procedure
From the top bar, select the signed-in user, then select Change Password.

In the Change Password dialog, set the properties described in the Change a local user password topic.
Select Save.
Revoke local user tokens
If the user's existing tokens are compromised, you can revoke all the user's tokens, regardless of changing the user's password. To re-access the system, the user re-authenticates with the new password, or the user needs to obtain new tokens using the API.
Procedure
In the Local Users tab, select the three dots of the local user you want to revoke the user tokens, then select Revoke User Tokens.
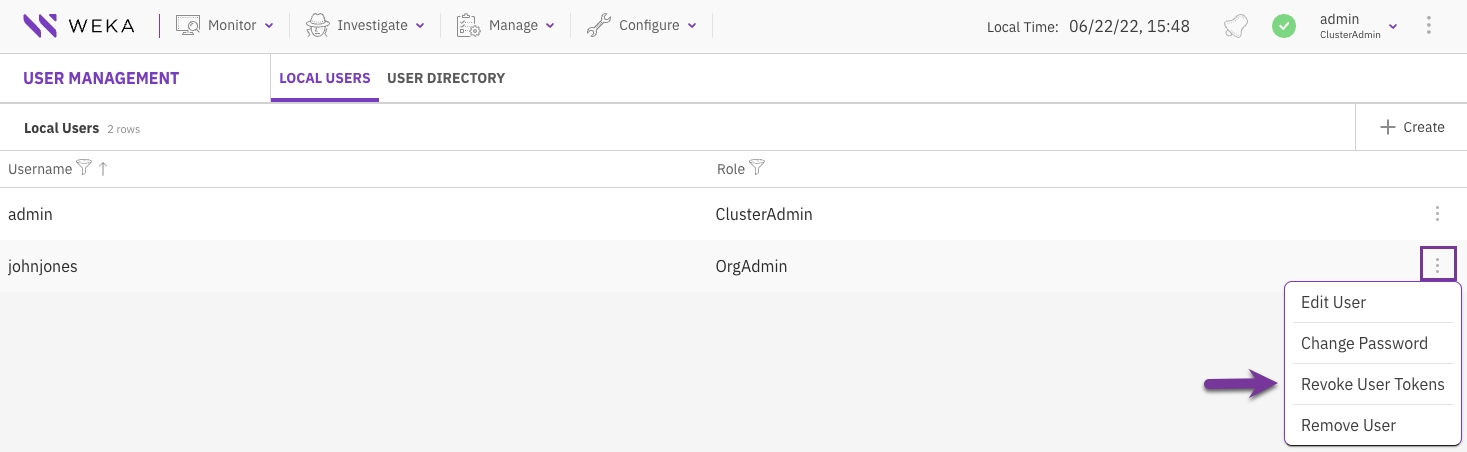
In the confirmation message, select Revoke Tokens.
Remove a local user
You can remove a local user that is no longer required.
Procedure
In the Local Users tab, select the three dots of the local user to remove, then select Remove User.

In the confirmation message, select Yes.
Configure LDAP/AD in WEKA
You can set the user access to the WEKA system from the organization user directory by Lightweight Directory Access Protocol (LDAP) or Active Directory (AD).
Integrate the WEKA system with your organization's user directory using either Lightweight Directory Access Protocol (LDAP) or Active Directory (AD) for centralized user authentication. This allows users to access the WEKA system with their existing credentials.
From the menu, navigate to Configure > User Management and select the User Directory tab. The system displays options to configure either LDAP or Active Directory.
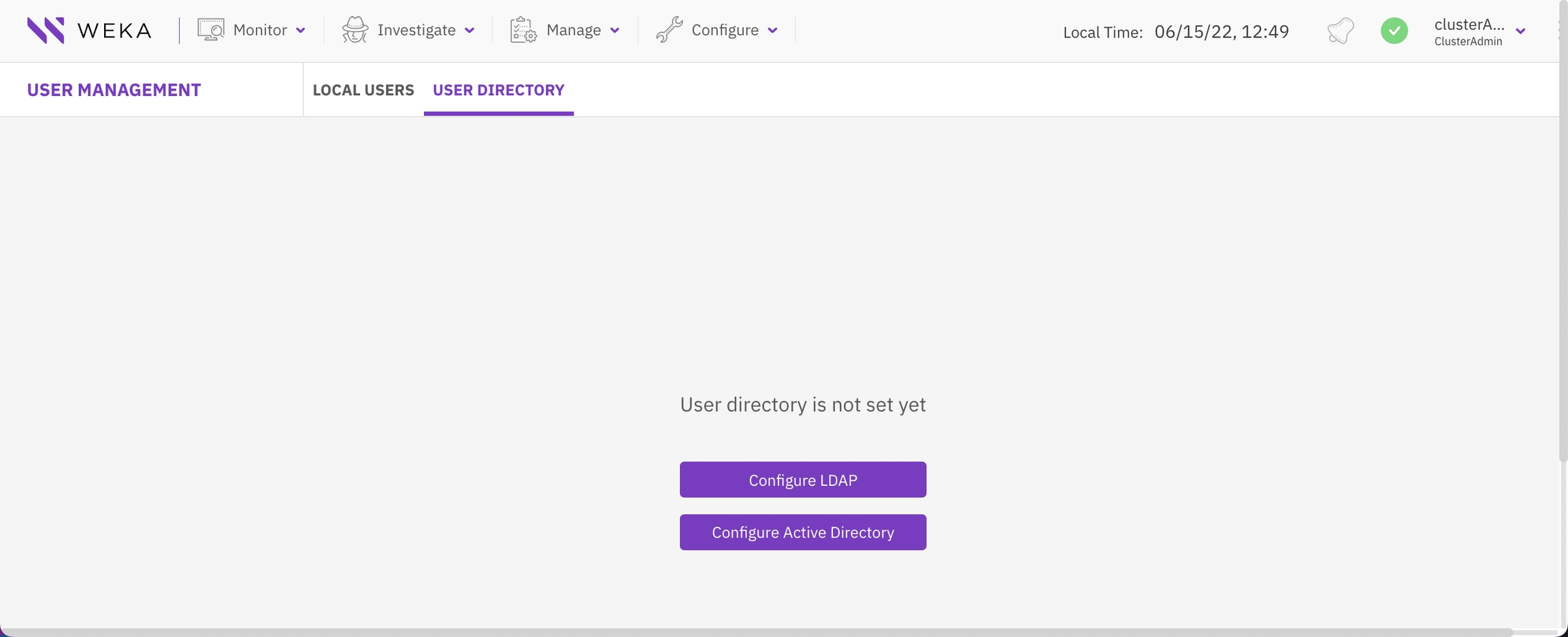
Configure LDAP
Connect to an LDAP server to authenticate and authorize users for access to the WEKA system.
Procedure
On the User Directory tab, select Configure LDAP.
In the Configure LDAP dialog, set the properties according to your LDAP environment. For details about each property, see the LDAP property reference.
Select Save.

After saving the configuration, the User Directory tab displays the LDAP connection details. From this view, you can update, disable, or reset the configuration.
Configure Active Directory
Connect to an Active Directory (AD) domain to authenticate and authorize users for access to the WEKA system.
Procedure
On the User Directory tab, select Configure Active Directory.
In the Configure Active Directory dialog, set the properties according to your AD environment. For details about each property, see the Active Directory property reference.
Select Save.

After saving the configuration, the User Directory tab displays the Active Directory connection details. From this view, you can update, disable, or reset the configuration.
Last updated