Manage KMS using GUI
Explore procedures for managing Key Management System (KMS) integration with the WEKA system using the GUI.
Using the GUI, you can:
Configure a KMS
Configure the KMS of either HashiCorp Vault or KMIP within the WEKA system to encrypt filesystem keys securely.
Before you begin
Ensure the KMS is preconfigured, and the key and a valid token are readily available.
Procedure
From the menu, select Configure > Cluster Settings.
From the left pane, select Security.
On the Security page, select Configure KMS.
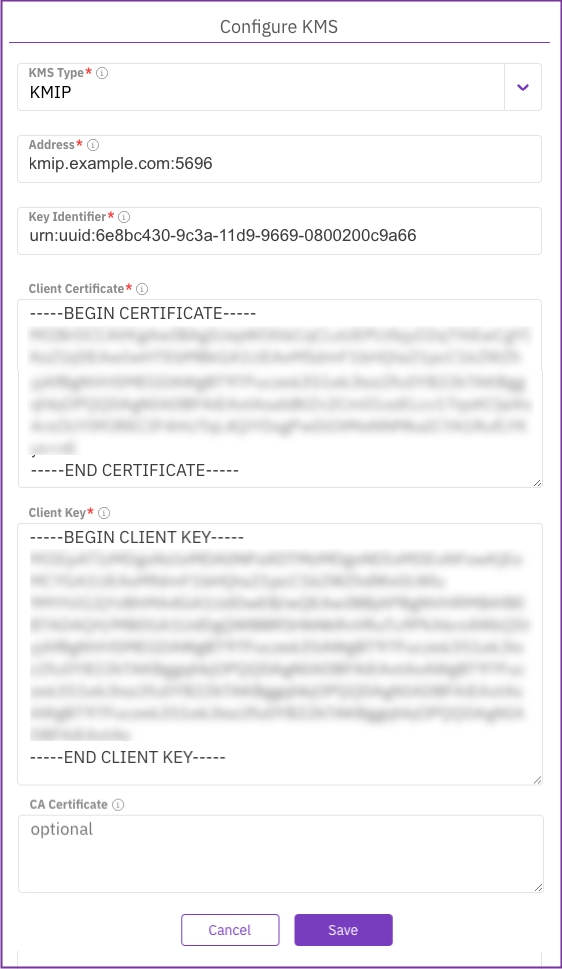
On the Configure KMS dialog, select the KMS type to deploy: HashiCorp Vault or KMIP.
Set the connection properties according to the selected KMS type. Select the relevant tab for details:
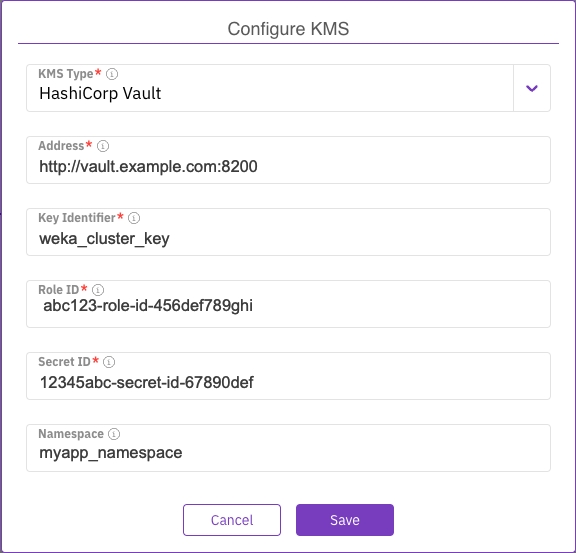
To configure the HashiCorp Vault connection from the GUI, set the following properties.
Address: The KMS server address.
Key Identifier: The key name used to secure the filesystem keys.
Role ID: The Role ID for AppRole authentication, provided by the Vault administrator.
Secret ID: The Secret ID for AppRole authentication, provided by the Vault administrator.
Namespace: The namespace in Vault that identifies the logical partition for organizing data and policies. Namespace names must not end with
/, avoid spaces, and refrain from using reserved names likeroot,sys,audit,auth,cubbyhole, andidentity.
Select Save.
Related topics
Obtain an API token from the vault
Obtain a certificate for a KMIP-based KMS
View the KMS configuration
Procedure
From the menu, select Configure > Cluster Settings.
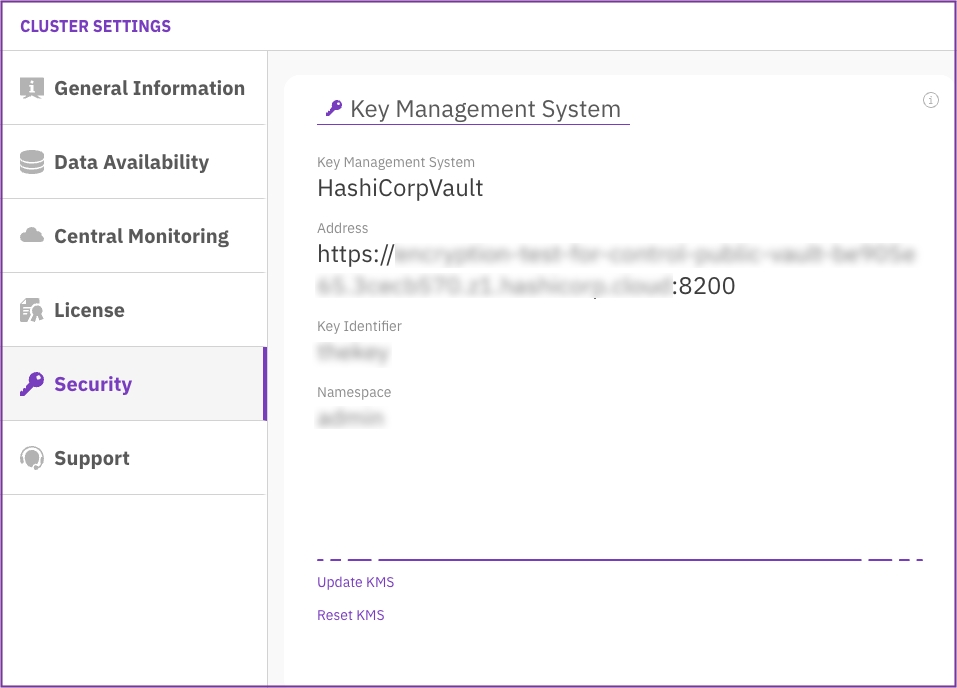
From the left pane, select Security. The Security page displays the configured KMS.
Update the KMS configuration
Update the KMS configuration in the WEKA system when changes occur in the KMS server details or cryptographic keys, ensuring seamless integration and continued secure filesystem key encryption.
Procedure
From the menu, select Configure > Cluster Settings.
From the left pane, select Security.
The Security page displays the configured KMS.
Select Update KMS, and update the settings. For the parameter descriptions, see Configure a KMS.
Select Save.
Reset the KMS configuration
Reseting a KMS configuration is possible only if no encrypted filesystems exist.
Procedure
From the menu, select Configure > Cluster Settings.
From the left pane, select Security.
The Security page displays the configured KMS.
Select Reset KMS.
In the message that appears, select Yes to confirm the KMS configuration reset.
Last updated