Manage TLS certificates
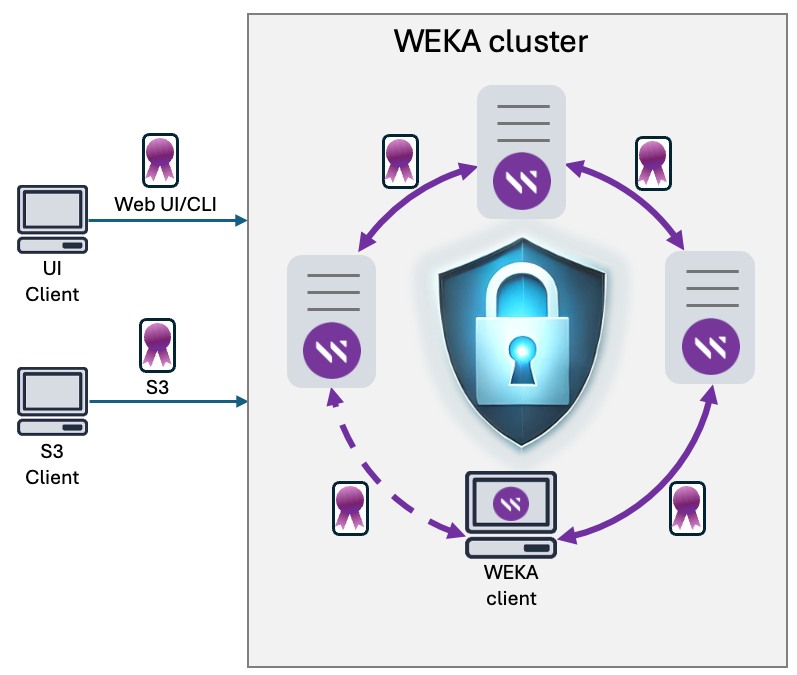
Manage TLS certificates to encrypt data in transit and verify system identity, ensuring secure communication in the WEKA cluster.
Last updated
Manage TLS certificates to encrypt data in transit and verify system identity, ensuring secure communication in the WEKA cluster.

Last updated